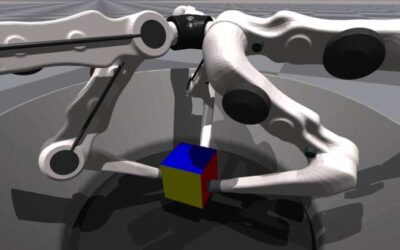
Last year, the Max Planck Institute for Intelligent Systems organized the Real Robot Challenge, a competition that challenged academic labs to come up with solutions to the problem of repositioning and reorienting a cube using a low-cost robotic hand. The teams...
Computer Sciences
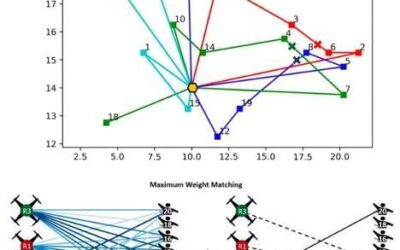
An online method to allocate tasks to robots on a team during natural disaster scenarios
Teams of robots could help users to complete numerous tasks more rapidly and efficiently, as well as keeping human agents out of harm's way during hazardous operations. In recent years, some studies have particularly explored the potential of robot swarms in assisting...
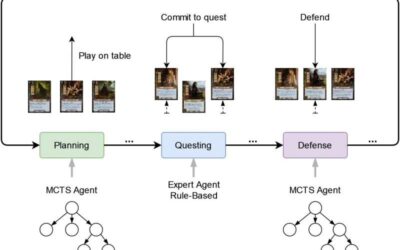
Monte Carlo tree search algorithms that can play the Lord of the Rings card game
When machine learning algorithms and other computational tools started becoming increasingly advanced, many computer scientists set out to test their capabilities by training them to compete against humans at different games. One of the most well-known examples is...
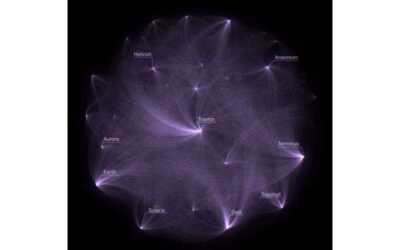
Turning an analysis of Asimov’s Foundation into art
In recent years, numerous computer scientists and artists worldwide have worked on projects that merge digital art and computer science. For instance, some introduced computational models that can create original artworks, while others used data analysis tools to...
A framework to enhance deep learning using first-spike times
Researchers at Heidelberg University and University of Bern have recently devised a technique to achieve fast and energy-efficient computing using spiking neuromorphic substrates. This strategy, introduced in a paper published in Nature Machine Intelligence, is a...
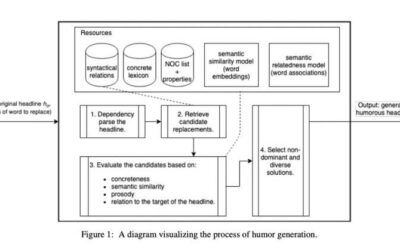
A model that can generate humorous versions of existing headlines
Over the past decade or so, computer scientists have developed a growing number of computational models that can generate, edit and analyze texts. While some of these models have achieved remarkable results, some aspects of human language and communication have proved...
Baby Robot: A system that helps toddlers practice their motor skills
Researchers at Universitat Politecnica de Catalunya in Barcelona have recently developed Baby Robot, a robotic toy that could be used to enhance the motor skills of toddlers. This system, presented in a paper pre-published on arXiv, can interact with toddlers in ways...
DronePaint: A human-swarm interaction system for environment exploration and artistic painting
Researchers at Skolkovo Institute of Science and Technology (Skoltech) in Russia have recently developed an innovative system for human-swarm interactions that allows users to directly control the movements of a team of drones in complex environments. This system,...
An autonomous system that can reach charge mobile robots without interrupting their missions
Researchers at Skolkovo Institute of Science and Technology in Russia have recently developed MobileCharger, an autonomous robotic system designed to charge other robots as they complete their missions. This system, presented in a paper pre-published on arXiv, can...
A robot vision system that diminishes occlusions using mirror reflections
To navigate their surroundings safely and most effectively, robots should be supported by a highly performing computer vision system. One of the greatest challenges when developing computer vision systems for robots is to limit occlusions so that the robot can sense...