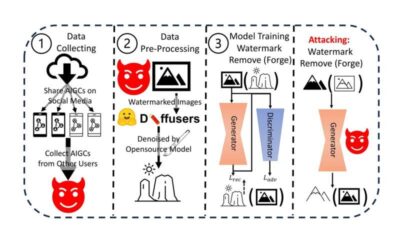
With the advent of LensaAI, ChatGPT and other highly performing generative machine learning models, the internet is now growing increasingly saturated with texts, images logos and videos created by artificial intelligence (AI). This content, broadly referred to as AI...
Security
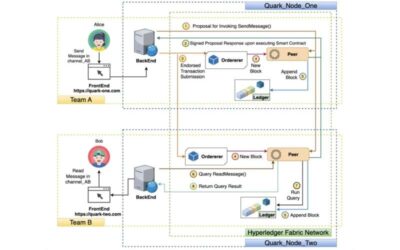
A decentralized, blockchain-based messaging network for safer communications
Data and security breaches are becoming increasingly common, highlighting the vulnerabilities of existing messaging and communications platforms. Devising computational tools and systems that better protect sensitive data against malicious attacks is therefore of...
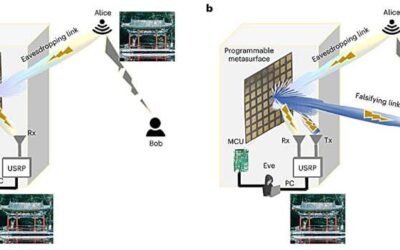
Study highlights the vulnerabilities of metasurface-based wireless communication systems
Metasurfaces, artificially engineered surfaces that can manipulate electromagnetic signals in unique ways, have huge potential for several technological applications, including the implementation of sixth generation (6G) cellular communications. The limitations and...
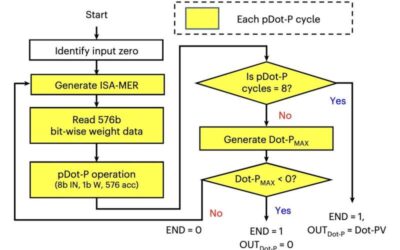
A CMOS-compatible spintronic compute-in-memory macro to secure AI edge devices
Edge computing applications, which entail the processing and storage of data at the source of its production (i.e., near where it is created), is now being applied to a growing number of technologies. The application of edge computing translates into devices that can...
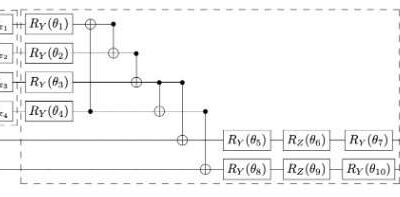
Study tests the potential of two quantum machine learning algorithms for malware classification
Over the past decades, cyber attackers have become increasingly skilled at compromising systems and circumventing security measures. As a result, detecting and accurately identifying malware is a pressing challenge for many businesses and individuals worldwide.
A review of existing studies investigating online romance fraud
Online romance fraud is an increasingly common phenomenon, which can affect people of all ages worldwide. This type of fraud occurs when a malicious individual or members of a criminal organization engage with users online pretending to be romantically interested in...
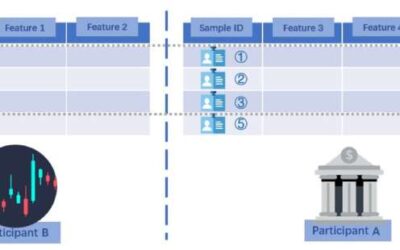
A new inference attack that could enable access to sensitive user data
As the use of machine learning (ML) algorithms continues to grow, computer scientists worldwide are constantly trying to identify and address ways in which these algorithms could be used maliciously or inappropriately. Due to their advanced data analysis capabilities,...
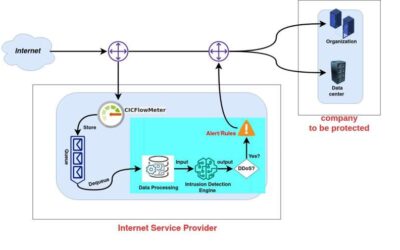
A new AI-based tool to detect DDoS attacks
Cybercriminals are coming up with increasingly savvy ways to disrupt online services, access sensitive data or crash internet user's devices. A cyber-attack that has become very common over the past decades is the so-called Distributed Denial of Service (DDoS) attack.
A three-stage authentication system for the metaverse
In recent years, many computer scientists have been exploring the notion of metaverse, an online space in which users can access different virtual environments and immersive experiences, using VR and AR headsets. While navigating the metaverse, users might also share...
An architecture that gives users full control of their smartphones
In recent years, many smartphone users have become concerned about the privacy of their data and the extent to which companies might have access to this data. As things stand today, the applications that users can run on their phone and what they can do with these...