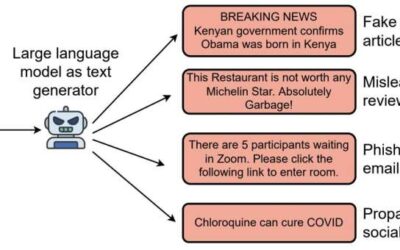
Advances in the field of machine learning have recently enabled the development of computational tools that can create convincing but artificially produced texts, also known as deepfake texts. While the automatic creation of texts could have some interesting...
Security
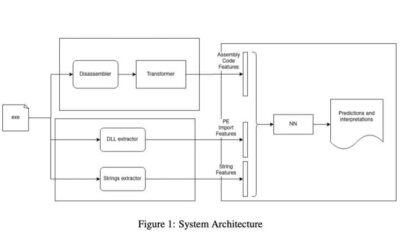
The vulnerability of transformers-based malware detectors to adversarial attacks
Cyber attackers are coming up with increasingly sophisticated techniques to steal users' sensitive information, encrypt documents to receive a ransom, or damage computer systems. As a result, computer scientists have been trying to create more effective techniques to...
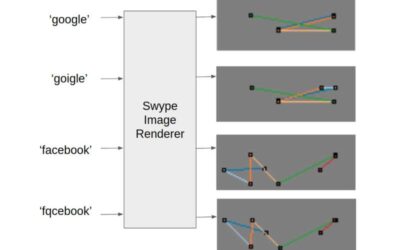
TypoSwype: An image recognition tool to detect typosquatting attacks
In recent decades, cyberattacks have become increasingly varied, introducing various strategies to lure users onto malicious websites or prompt them to share sensitive data. As a result, computer scientists are continuously trying to develop more advanced tools to...
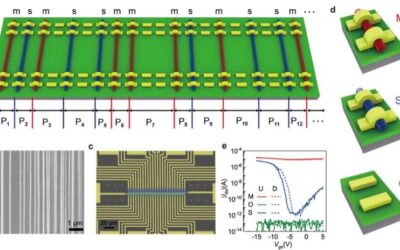
Twin physically unclonable functions (PUFs) based on carbon nanotube arrays to enhance the security of communications
As the amount of data stored in devices and shared over the internet continuously increases, computer scientists worldwide are trying to devise new approaches to secure communications and protect sensitive information. Some of the most well-established and valuable...
A deep learning technique to generate DNS amplification attacks
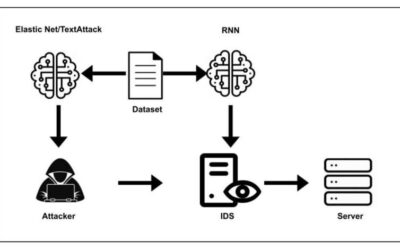
Deep learning techniques have recently proved to be highly promising for detecting cybersecurity attacks and determining their nature. Concurrently, many cybercriminals have been devising new attacks aimed at interfering with the functioning of various deep learning...
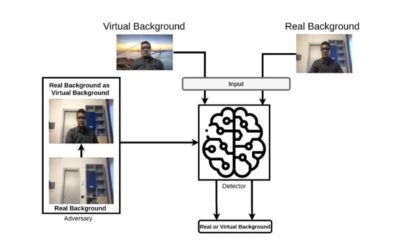
A strategy to discern between real and virtual video conferencing backgrounds
Video-conferencing platforms such as Skype, Microsoft Teams, Zoom and Google Meet allow people to communicate remotely with others in different parts of the world. The COVID-19 pandemic and the social distancing measures that followed led to a further rise in the use...
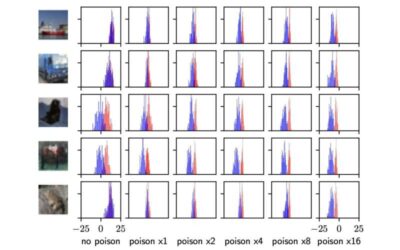
The risks of attacks that involve poisoning training data for machine learning models
A growing number of studies suggest that machine learning algorithms can leak a considerable amount of information included in the data used to train them through their model parameters and predictions. As a result, malicious users with general access to the algorithm...
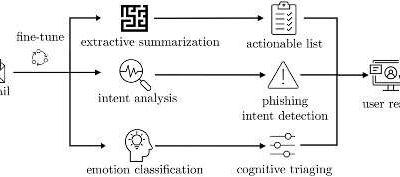
A model that can help inexperienced users identify phishing emails
Phishing attacks are cyber-attacks through which criminals trick users into sending them money and sensitive information, or into installing malware on their computer, by sending them deceptive emails or messages. As these attacks have become increasingly widespread,...
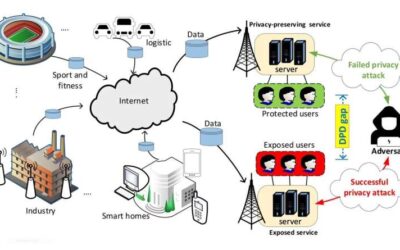
Study shows that online privacy has become a cause of inequality
As information and communications technology (ICT) systems proliferate, it has become essential for the privacy of users to be considered and safeguarded. While there are many existing ways to protect users' digital privacy, such as network security measures,...
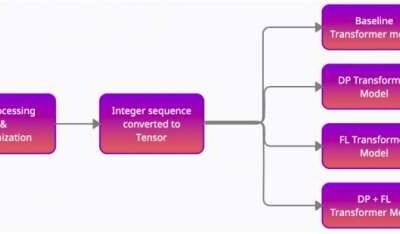
A model to classify financial texts while protecting users’ privacy
Over the past decade or so, computer scientists developed a variety of machine learning (ML) models that can analyze large amounts of data both quickly and efficiently. To be applied in real-world situations that involve the analysis of highly sensitive data, however,...