Researchers at IBM have recently devised a new technique to virtually patch security vulnerabilities before they are found. Their approach, presented at the International Workshop on Information and Operational Technology, co-located with RAID18, leverages testing...
Security
Box of Pain: A new tracer and fault injector for distributed systems
In computer science, distributed systems are systems with components located on different devices, which communicate with one another. While these systems have become increasingly common, they are typically filled with bugs.
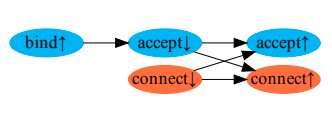
Circular all-or-nothing: A new approach to protect data from key exposure
A team of researchers at Telecom ParisTech has developed a new method to protect encrypted data against key exposure. Their algorithm, presented in a paper pre-published on arXiv, transforms, fragments and disperses data so that it remains protected, unless all...
A model to classify cyberattacks using swarm intelligence
In recent years, new technological advances have led to a growing number of devices, ranging from more conventional computers to other gadgets and smart home appliances, communicating and sharing data with one another. Despite its advantages, this growing...
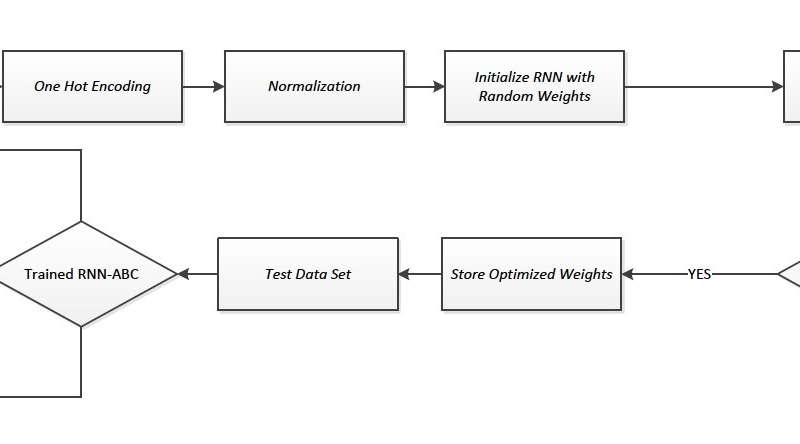
Using machine learning to detect software vulnerabilities
A team of researchers from R&D company Draper and Boston University developed a new large-scale vulnerability detection system using machine learning algorithms, which could help to discover software vulnerabilities faster and more efficiently.
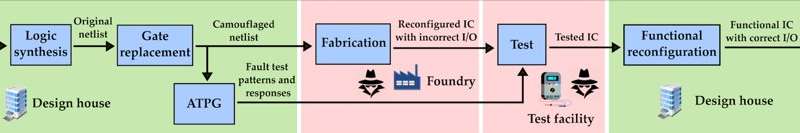
A dynamic camouflaging approach to prevent intellectual property theft
In recent years, hardware-centric security threats have emerged at different stages of the integrated circuit (IC) supply chain. This has enabled the proliferation of various malicious attacks, such as intellectual property (IP) piracy, illegal overproduction of ICs,...