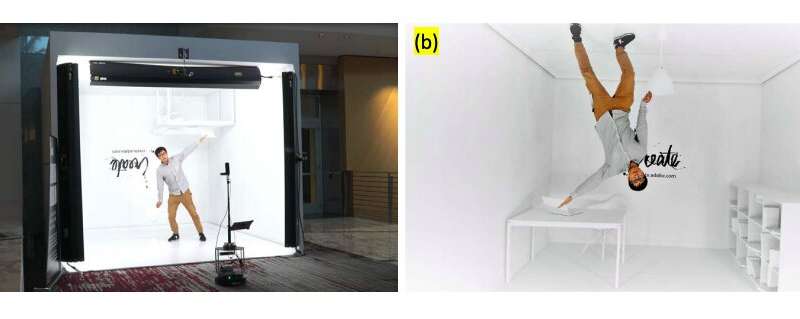
Taking good-quality photographs can be a challenging task, as it typically requires finding ideal locations, angles and lighting conditions. Although artistic pictures have so far primarily been taken by human photographers, in recent years, some researchers have...
TECHXPLORE
Maestro: a new attack that orchestrates malicious flows with BGP
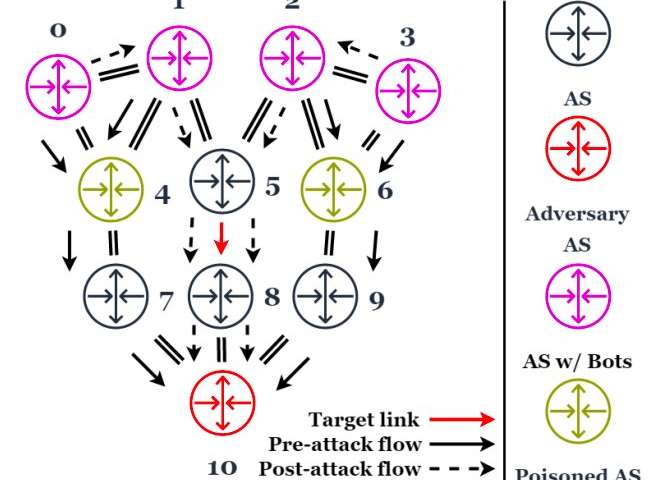
Researchers at the University of Tennessee have recently identified the Maestro attack, a new link flooding attack (LFA) that leverages plane traffic control engineering techniques to concentrate botnet-sourced distributed denial of service (DDos) flows on transit...
MobiKa: A low-cost mobile robot that can assist people in a variety of settings
Researchers at Fraunhofer IPA, in Stuttgart, Germany, have recently developed MobiKa, a low-cost, mobile robot capable of two-modal (voice and text) interactions with humans. Their robot, presented in a paper pre-published on arXiv, could be particularly useful for...
Monitoring human physiological responses to improve interactions with robots
Researchers from the Century Mold Collaborative Robotics Laboratory (CMCRL) at Rochester Institute of Technology (RIT) in New York have recently developed a new framework for monitoring human physiological responses while users are collaborating with a robot to...
Generating cross-modal sensory data for robotic visual-tactile perception
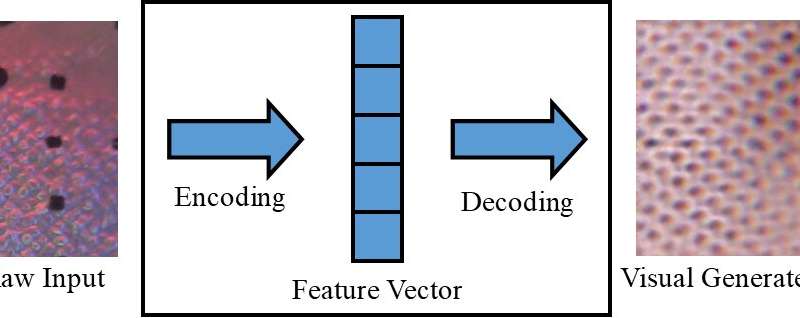
Perceiving an object only visually (e.g. on a screen) or only by touching it, can sometimes limit what we are able to infer about it. Human beings, however, have the innate ability to integrate visual and tactile stimuli, leveraging whatever sensory data is available...
Highly performing and wafer-scalable aligned carbon nanotube transistors
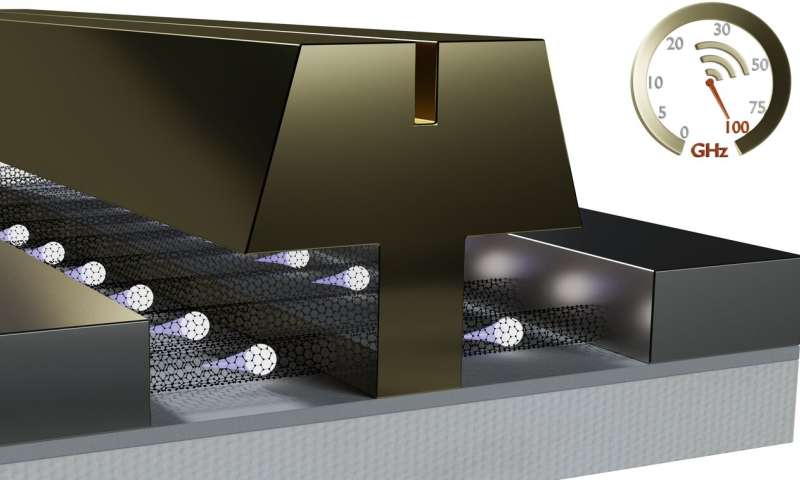
As we enter the wireless world of 5G, communications in the millimeter-wave band (i.e., from 30 to 300 GHz) will become increasingly important, particularly for high-speed wireless data-transfer applications. The trouble is that at these small wavelengths, the...
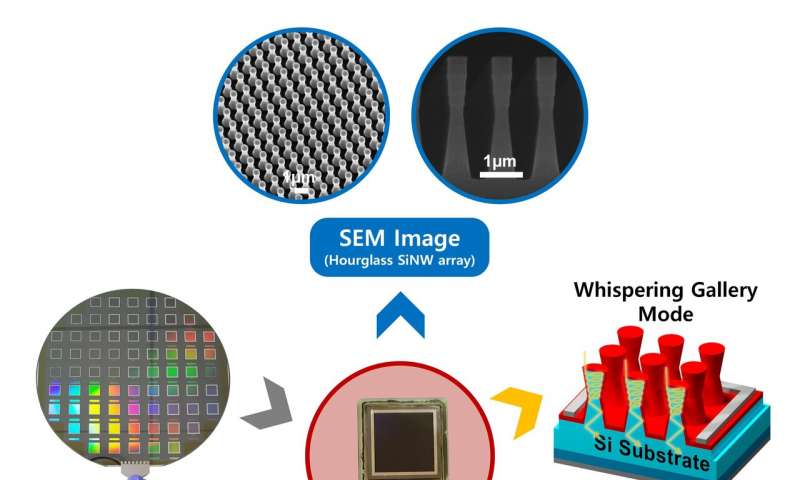
Hourglass-shaped silicon photodiodes with an enhanced near-infrared photoresponse
Silicon photodiodes are semiconductor devices commonly used to detect visible light and measure its intensity, color and position. The fact that these devices are made of silicon has both advantages and disadvantages.
How people’s stance on a topic can be inferred from their online activity
As proven by some recent extreme, controversial incidents, such as the Facebook and Cambridge Analytica scandal, social media can be a real goldmine for user information. In fact, most social researchers and analytics companies perceive social media as one of the most...
IBM researchers develop a technique to virtually patch vulnerabilities ahead of threat
Researchers at IBM have recently devised a new technique to virtually patch security vulnerabilities before they are found. Their approach, presented at the International Workshop on Information and Operational Technology, co-located with RAID18, leverages testing...
Distilled 3-D (D3D) networks for video action recognition
A team of researchers at Google, the University of Michigan and Princeton University have recently developed a new method for video action recognition. Video action recognition entails identifying particular actions performed in video footage, such as opening a door,...