Security researchers at Imperva yesterday said that a number of home routers have been hijacked by a new Mirai-based botnet, with 99% of them belonging to TalkTalk customers.
Security
Cyber criminals boast on dark web about Tesco Bank breach
Hackers called Tesco Bank a "cash milking cow" and "easy to cash out" in posts on dark web forums months before this week's attack, according to cybersecurity firm Cyberint.
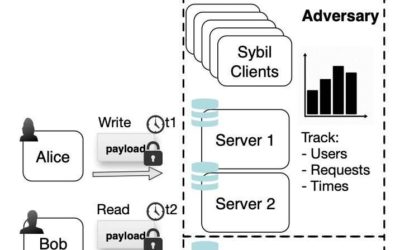
Talek: A private messaging system that hides message contents and user communication patterns
Encrypted messaging services, which prevent cyberattackers from reading the contents of messages exchanged by their users, have become increasingly popular over the past decade or so. While these services hide message content, malicious users can often use the network...
Cyber criminals boast on dark web about Tesco Bank breach
Hackers called Tesco Bank a "cash milking cow" and "easy to cash out" in posts on dark web forums months before this week's attack, according to cybersecurity firm Cyberint.
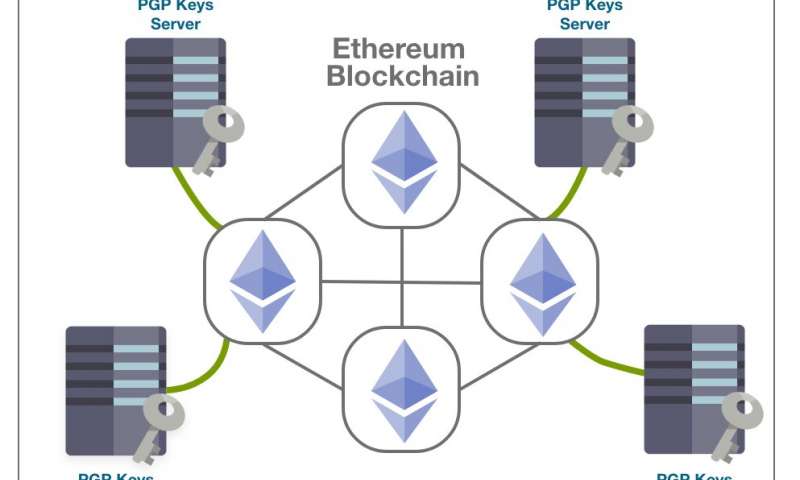
BlockPGP: A new blockchain-based PGP management framework
Pretty Good Privacy (PGP), one of the most widely used cryptographic standards, enables safe end-to-end encryption for emails, messages and other data sharing between users. Essentially, PGP works by implementing asymmetric encryption, in which certificates are shared...
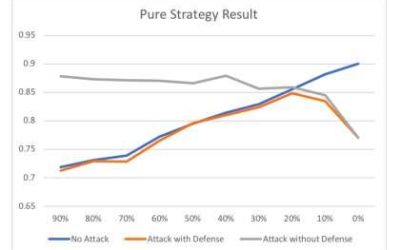
Using game theory to model poisoning attack scenarios
Poisoning attacks are among the greatest security threats for machine learning (ML) models. In this type of attack, an adversary tries to control a fraction of the data used to train neural networks and injects malicious data points to hinder a model's performance.
Randpay: a technology for blockchain micropayments that requires a recipient’s consent
Two researchers at Emercoin, a decentralized peer-to-peer (p2p) network providing secure blockchain business services, have recently developed a new technology called Randpay that only allows users to complete payments and transactions with a recipient's consent....
Selecting the best features for phishing attack detection algorithms
In recent decades, phishing attacks have become increasingly common. These attacks allow attackers to obtain sensitive user data, such as passwords, usernames, credit card details, etc., by tricking people into disclosing personal information. The most common type of...
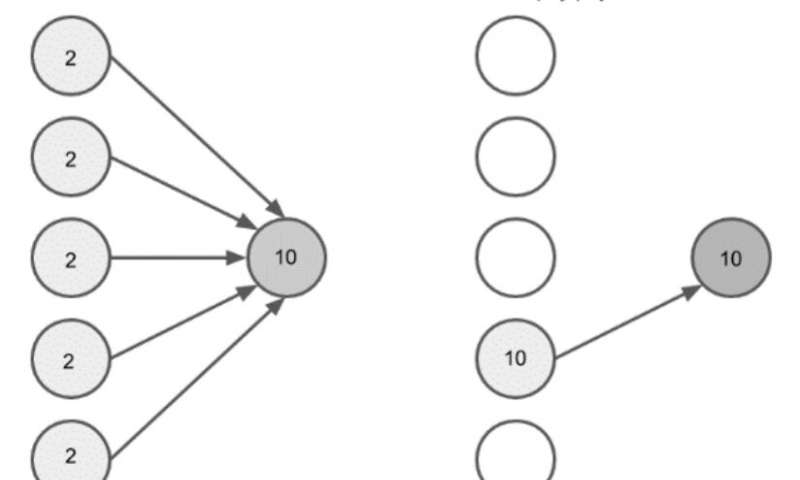
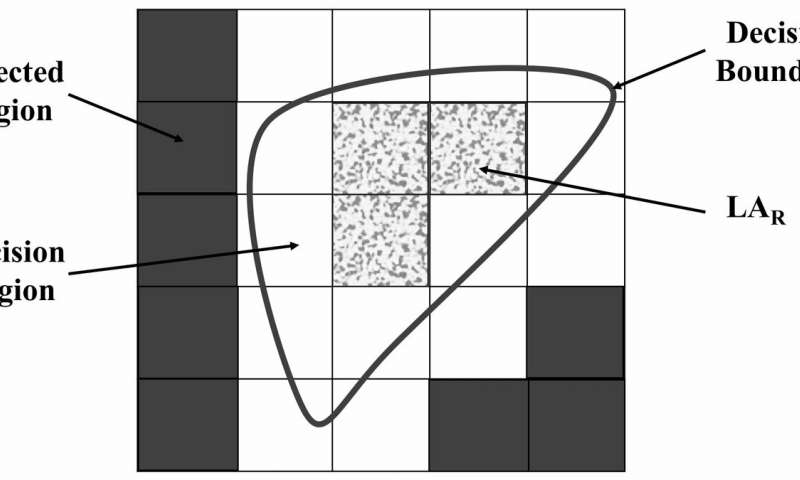
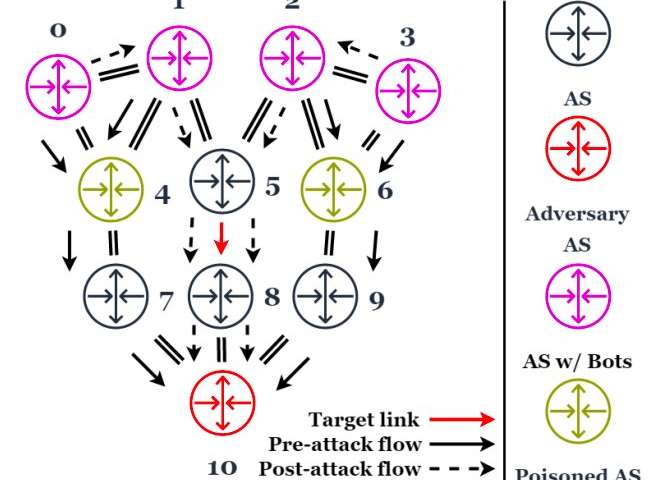
Maestro: a new attack that orchestrates malicious flows with BGP
Researchers at the University of Tennessee have recently identified the Maestro attack, a new link flooding attack (LFA) that leverages plane traffic control engineering techniques to concentrate botnet-sourced distributed denial of service (DDos) flows on transit...
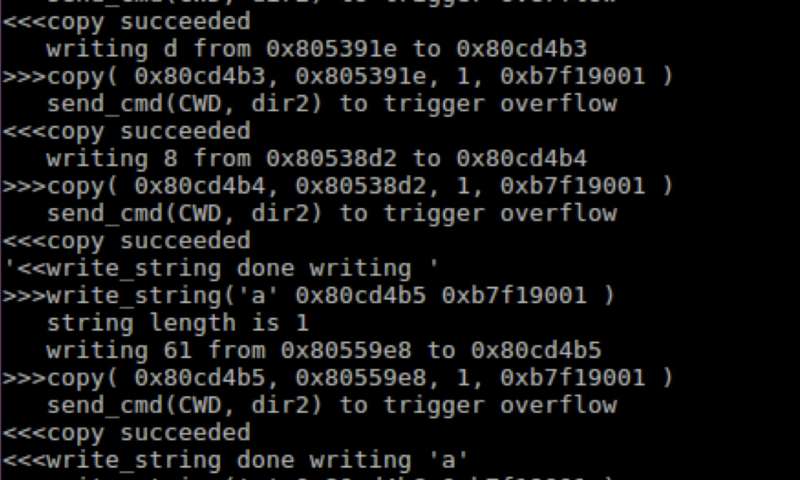
New exploitation techniques and defenses for DOP attacks
Data-oriented attacks allow hackers to manipulate non-control data and alter a program's behavior, often causing significant damage to the systems affected. Researchers at Virginia Tech, Clemson University, Pennsylvania State University and Aalto University have...